Twitter Admin Panel Screenshots
On July 15th, 2020 a hacker gained access to Twitter’s network to gain control over dozens of high-profile Twitter accounts. These accounts included business leaders, celebrities, and political actors like Barack Obama, Kim Kardashian, Jeff Bezos, and Elon Musk. Through a series of “double your bitcoin” scams, the hackers were able to steal $118,000 worth of bitcoin.
This hacker also obtained and released screenshots of Twitter’s ‘admin panel’. These screenshots show nonpublic, internal features Twitter uses to limit accounts that violate Twitter’s Rules over user conduct and allegedly reduce a user’s visibility in Twitter Trends and Search.
Editor’s Note: This post was originally published in July 2020 and has been updated for accuracy and comprehensiveness.
UPDATE: New York State Department of Financial Services releases investigation report into the Twitter ‘admin panel’ and bitcoin scam breach
The most recent news on the Twitter breach and admin panel leaks came from the New York Department of Financial Services (DFS) investigation report. Released on October 14th, 2020, the report profiled the entire attack, gave facts about the attack, a visual timeline, and weaknesses in Twitter’s security setup that led to the attack.
Governor Cuomo asked the NYDFS to investigate the hack on July 16th, citing cybersecurity and elections concerns. In summary, NYDFS called for increased regulation of social media companies, saying, “Our public institutions must evolve to keep up with new types of systemically important systems such as social media. The need for a new regulatory framework is clear.”
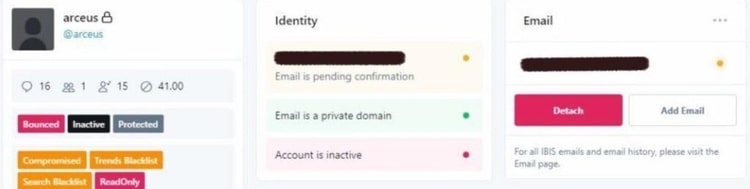
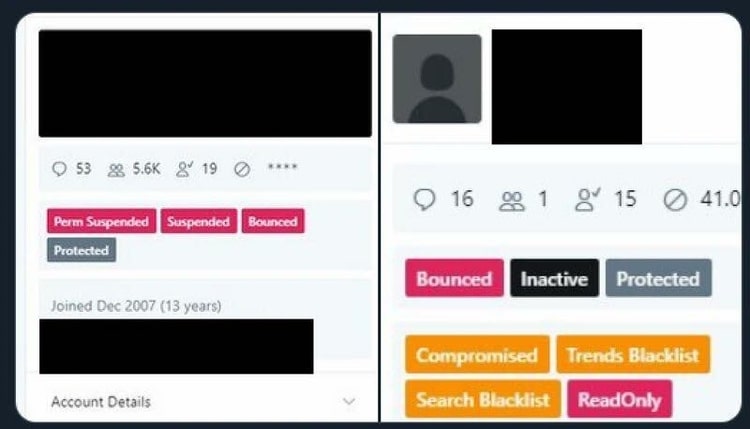
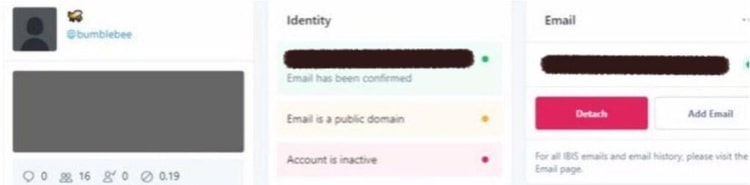
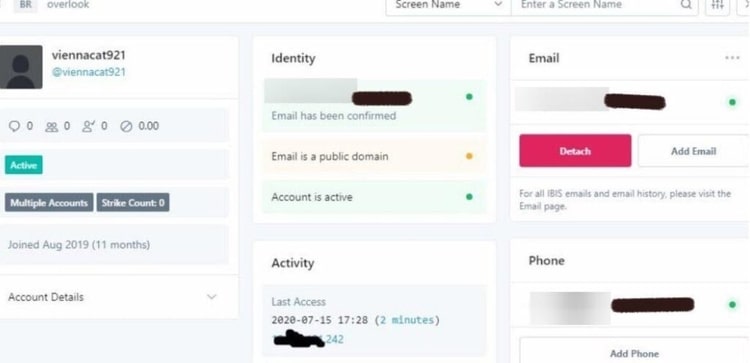
Screenshot images of Twitters internal ‘admin panel’ tool
Confirmed and unconfirmed screenshots from Twitter’s internal admin panel tool. Twitter was reported to have suspended and removed accounts that posted screenshot images of the tool within the microblogging site.
How did the breach happen?
Reports from Twitter and the NY Department of Financial Services stated this breach was a result of social engineering.
One or more hackers contacted Twitter employees impersonating Twitter’s IT Help Desk department. The hackers told the Twitter employee they were working on an issue with a VPN (a common issue among Twitter staff in 2020). They instructed the employee to visit a phishing website disguised as a legitimate VPN website.
After taking control over the user account password administrator tools, the hackers turned their focus to the single letter, word, and number accounts called “OG” Twitter accounts. According to the investigation, hackers allegedly discussed selling these OG accounts for bitcoin.
The final phase of the attack involved the hackers using high-profile Twitter accounts to launch fake bitcoin-related scams. These scams resulted in the hackers taking $118,000 worth of bitcoin.
What do the screenshots of the admin panel reveal about Twitter?
The leaked screenshots of these internal systems reveal some of the methods by which Twitter controls the ebb and flow of information on their site.
‘Tags’ on the panel reveal “Trends Blacklist” and “Search Blacklist” functionality. These tags allegedly allow Twitter admins to reduce the reach and impressions of deemed undesirable content on the platform. Blocking an individual user’s visibility in trends and search reduces the ability for the user to ‘go viral’.
Twitter has been adamant in the past they do not limit the reach of accounts on their platform (called ‘shadow banning’). In 2018, Legal, Policy, and Trust & Safety Lead Vijaya Gadde of Twitter said in a blog post, “We do not shadow ban.”
Final thoughts in 2021 on the Twitter breach and captured images
A natural question arose in the aftermath of the attack: if hackers were powerful enough to gain access to the most important political communication tool in the world, used by leaders all over the nation to communicate with constituents…why did the hackers run a relatively small scale Bitcoin scam? Why did they only take $118,000 worth of Bitcoin?
We can be thankful the damage to the geopolitical scene was limited. But one can wonder; why was the damage limited? With a little imagination, it’s possible to game-theory far worse outcomes. Elon Musk could have announced he is leaving the company, tanking the stock, allowing for short sales. What if President Donald Trump had tweeted his intention to go to war with another nation, leading to possible conflict?
This is just scratching the surface of possibilities.
The focus of the investigation by the NYFDS was on the breach and the result of the cryptocurrency scam. The admin panel screenshots were hardly addressed – even though they bring up an interesting larger point with speech regulation on Twitter’s platform. Large social media companies, including Twitter, have long been suspected of being politically motivated when it comes to suspensions, censorship of content, and suppression of reach.
The end result of this hack is more questions. We may never know the full story.
Hi there! Did you enjoy this article? Subscribe to our mailing list so we don't lose touch!




